
New DORA regulations come into force on January 17th, 2025 for all financial institutions within the EU and UK entities with cross-border activities.
In the first article of this series, we examine the challenges DORA presents for many organisations around the ICT Risk Management section of the regulations.
What is DORA?
DORA, (the Digital Operations Resilience Act) is a set of binding regulations which apply to all financial institutions in EU member states and those operating across its borders. The regulations have been brought in as an acknowledgement that ICT incidents and a lack of operational resilience have the potential to endanger the integrity of the entire EU financial system.
The penalties for non-compliance with DORA can be more severe than other regulations. Financial institutions can be fined up to 10 million euros or 2% of their total annual turnover, whichever is higher, for serious regulation infringements.
Another penalty that differs from other ICT security regulations is that, under DORA, individuals such as CISOs or COOs can also be penalised with heavy fines, resulting in damage to their reputation.
This article focuses on the key weaknesses Chief Information Security Officers and Chief Operating Officers need to address around the ICT Risk Management section of the Act.
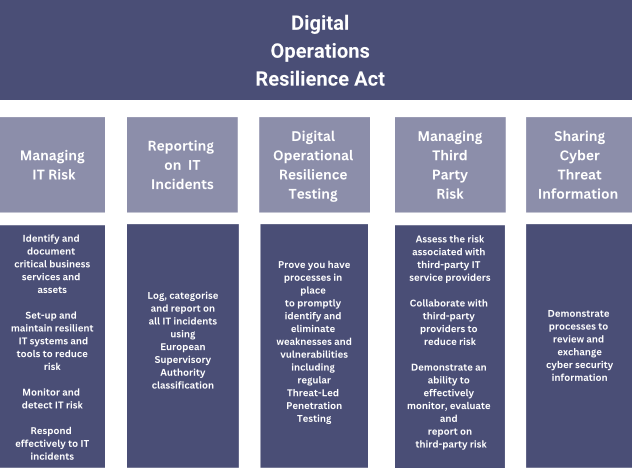
An Overview of the Digital Operations Resilience Act
Achieving DORA Compliance around ICT Risk Management
The ICT Risk Management section of DORA regulations states the necessity for organisations to ‘set up and maintain resilient ICT systems and tools that minimise the impact of ICT risk’.
Replacing legacy systems with ICT products which have been shown to minimise risk is therefore a worthwhile step for organisations to demonstrate their resilience. Tools which increase visibility will also support organisations in the continuous monitoring required as part of DORA ICT Risk Management and the ICT-related incident management, classification, and reporting.
Putting plans in place for periodic maintenance will also be necessary for compliance around ICT Risk Management, which we cover in a separate article ‘DORA compliance: Operational Resilience and the role of ICT Maintenance.’
Reducing Risk around File Transfer
Data security should already be a top priority for financial organisations. IBM research shows that the cost of breaches is rising and that breaches are becoming more common, with 51% of organisations experiencing data breaches within the past year. In fact, many financial organisations have been recently affected by critical vulnerabilities in the Progress Software product MOVEit for Managed File Transfer (MFT) which potentially exposed data to hackers.
Article 9.3 in the ICT Risk Management section of the DORA regulations addresses maintaining operational resilience around data transfer:
‘a) ensure the security of the means of transfer of data.
(b) minimise the risk of corruption or loss of data, unauthorised access and technical flaws that may hinder business activity.
(c) prevent the impairment of the authenticity and integrity, the breaches of confidentiality and the loss of data.
(d) ensure that data is protected from risks arising from data management, including poor administration, processing-related risks, and human error.’
Weak points in security around data transfer for many organisations centre around one or more of the following three key areas:
1,Handling rapidly increasing volumes of data. Many enterprise file transfer systems aren’t built to handle such volumes of data as today’s financial institutions experience. The use of emerging technologies such as big data and expanding partner networks can also over-stress legacy file transfer systems, leading to errors and downtime.
2. A lack of ability to monitor data transfers end-to-end. This is often due to organisations using disparate, legacy systems to handle file transfer. In addition to being essential for compliance with monitoring requirements of DORA (section 3) visibility is key to operational resilience by identifying and resolving bottlenecks before they become system failures.
3. Failure to maintain a consistent, regular patching and upgrade schedule. Patches are released by the software developers to close security holes which have been identified in their products. Upgrades also protect systems against cyberattacks as old versions of software may contain cyphers which hackers have learned to crack, making your data vulnerable to exploitation.
For solutions to Reducing risk around file transfer and increasing resilience read our full article.
Achieving ‘Always On’ High-Availability
Managing the risk of downtime is high on the priority list for financial organisations as it impacts negatively on the customer experience, brand reputation, and in turn, revenue. Downtime also poses the risk of data loss, leading to compensation and regulatory fines.
The ICT Risk Management section of the DORA regulations addresses the importance of maintaining operational resilience to avoid data loss. Article 9.2 reads:
‘Financial entities shall design, procure and implement ICT security tools that aim to ensure the resilience, continuity and availability of ICT systems, in particular for those supporting critical or important functions, and to maintain high standards of availability, authenticity, integrity and confidentiality of data, whether at rest, in use or in transit.’
As file transfer is business-critical (financial organisations rely on the consistent, secure, and timely flow of documents) organisations will need to measure the reliability of their file transfer systems, (typically expressed as a percentage of time a machine remains in a working or available state) and demonstrate that poor availability has been addressed.
Implementing a B2B integration platform and data transfer systems which are proven to be highly resilient are key where organisations have poor availability rates which threaten data security.
Organisations should also look for a modern B2B platform which is scalable to cope with substantial increases in data transfer volumes and the larger file types associated with emerging technologies. It should also be capable of handling a wide variety of protocols used for transmitting data. This is particularly important when current data transfer systems experience bottlenecks, where the flow of data becomes blocked, leading to errors and downtime.
Read the full article Achieving High-Availability in MFT and DORA Compliance for solutions to this particular challenge.
Increasing Visibility in Managed File Transfer
The ICT Risk Management and the Incident Management, Classification and Reporting sections of the new Digital Operations Resilience Act require financial institutions to have a high degree of visibility around document and file transfer. However, using many different legacy systems to handle file transfer makes monitoring incredibly complex.
Under Article 16.1 of the DORA regulations, entities are required to:
‘continuously monitor the security and functioning of all ICT systems’ and ‘allow sources of ICT risk and anomalies in the network and information systems to be promptly identified and detected and ICT-related incidents to be swiftly handled.’
The key to meeting these requirements is integration. By consolidating a multiple, siloed payment system into a single file transfer solution, visibility, tracking and reporting data transactions of all types and industry standards (ISO, Visa, SWIFT etc) becomes much easier.
Organisations should look for a monitoring solution which gives an end-to-end, near-real-time view of the full file transfer cycle across a single screen. This better prepares financial entities to prevent ICT incidents from occurring and identify sources of risk. In turn, this increases reliability, allowing organisations to deliver the quality experience trading partners and customers expect.
Read our full article DORA Compliance: Increasing MFT Visibility for more information on this DORA challenge.
Discover how DORA may impact on your IT systems and remediation plans by booking a FREE SABREX DORA Consultation today.
Article by C.James